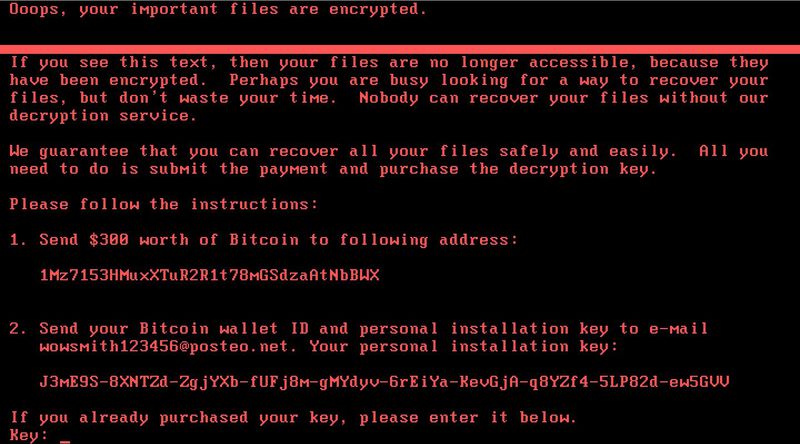
This is called ransomware, a relatively new form of malware that scrambles a victim’s files and then demands a payment to unscramble them.
Attacks like this have become an increasingly common problem online. Last month, thousands of computers were infected with ransomware that experts dubbed WannaCry, causing disruptions for hospitals in the United Kingdom.
Ars Technica’s Dan Goodin describes the carnage the software has caused:
It initially took hold in Ukraine and Russia, but soon it reportedly spread to Poland, Italy, Spain, France, India, and the United States. WPP, the British ad company, said on Twitter that some of its IT systems were hit by a cyber attack. Its website remained unreachable as this post was going live. Law firm DLA Piper posted a handwritten sign in one of its lobbies instructing employees to remove all laptops from docking stations and to keep all computers turned off. AV provider Avast said it detected 12,000 attacks so far. Security company Group-IB said at least 80 companies have been infected so far. Reuters also reported that a computer attack that hit Maersk, a shipping company that handles one in seven of all containers globally, caused outages at all of its computer systems across the world.
The new attack is sophisticated, making several improvements over the techniques used by last month’s WannaCry malware. The software steals credentials from victims’ computers and sends them back to a server controlled by the attackers.
Yet surprisingly, the attackers seem to have taken a lackluster approach to collecting ransom payments. That has caused some experts to doubt that the attackers were actually after money. Rather, they suspect that the hackers were trying to cause mayhem or steal data from selected targets, and that they simply used ransomware to sow confusion about the nature of the attack and who was behind it.
The latest outbreak may have been intended for destruction, not profit
The basic idea behind ransomware is simple: A criminal hacks into your computer, scrambles your files with unbreakable encryption, and then demands that you pay for the encryption key needed to unscramble the files. If you have important files on your computer, you might be willing to pay a lot to avoid losing them.
One of the hardest things about creating ordinary ransomware is the need to get ransom payments back from victims. Ransomware schemes have become a lot more effective since the invention of Bitcoin in 2009. Conventional payment networks like Visa and MasterCard make it difficult to accept payments without revealing your identity. Bitcoin makes that a lot easier. So the past four years have seen a surge in ransomware schemes striking unsuspecting PC users.
But an attack still needs infrastructure to receive and verify payments and then distribute decryption keys to victims — potentially thousands of them. And it needs to do this in a way that can’t be blocked or traced by authorities, which is why ransomware attackers often rely on the anonymous Tor network to communicate with victims.
But Posteo blocked access to this account, making it impossible for victims to reach the attackers. With no way to get a decryption key, there’s no incentive for victims to pay the ransom.
It’s possible that the perpetrators of this otherwise-sophisticated attack were naive about how to set up its payment system. But it’s also possible that they simply disguised the software as ransomware to camouflage the attack’s real purpose.
[“Source-vox”]
